OIDC (OpenID Connect) Structure
OIDC (OpenID Connect) Structure

Simple Identity Layer on top of the OAuth 2.0 Protocol.
OpenID Connect can be thought of as an identity layer added on top of the OAuth 2.0 protocol to enable the OAuth 2.0 protocol to be used for Authentication.
OpenID Connect contains a meta-data document (.well-known/openid-configuration) that defines the information required to login through an application. (Which urls should be used, which scopes it contains, etc.)
If you want to view the relevant metadata document as an example, you can access the Microsoft's OIDC metadata document by navigating to https://login.microsoftonline.com/common/v2.0/.well-known/openid-configuration.
As in OAuth 2.0, transactions are performed using flows in OIDC. As an example, let's examine the endpoints of Authorization Code Flow for OIDC as in OAuth 2.0.
Example: OAuth 2.0 - Authorization Code Flow
We can examine this flow in 6 steps:
1-) Authentication Request
- If we examine the related endpoint, we can see that a value called openid is passed in the scope section. We can actually think of this as the equivalent of the identity layer concept we used when defining OIDC. With this scope added to the OAuth 2.0 protocol, Authorization Server now handles the relevant request within the scope of OIDC.
2-) Authentication Response
- Here, as in OAuth 2.0, a GET request is sent to the callback-url (redirect-uri) with the
Authorization Code. In this way, the Client becomes aware of the relevant authorization code.
3-) Token Request
- Then, the relevant Client requests a token from the Authorization Server with the "authorization_code" it has obtained. (Token exchange => Authorization Code ↔ Access Token)
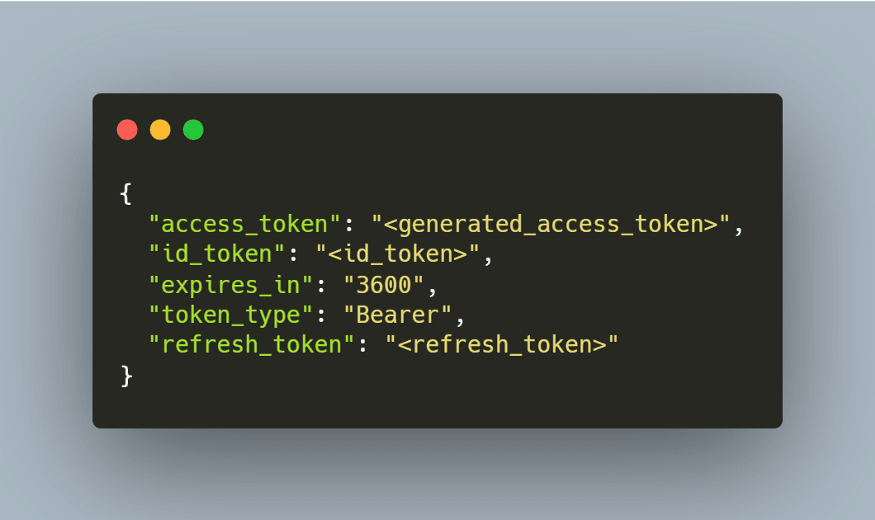
4-) Token Response
If we examine the response we can see the "id_token" section.
- ID_Token: It can be thought of as an identity card. Contains information about the end user. It is in JWT format. It can be thought of as the add-on that OIDC brings to OAuth 2.0. In this way, the Authentication process can happen.
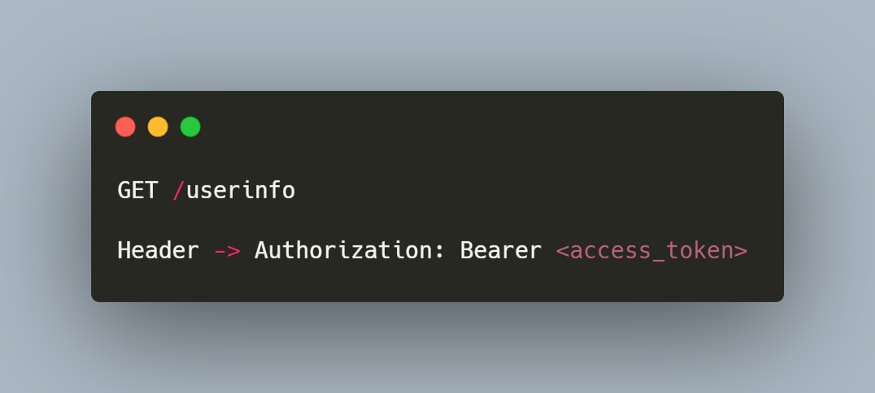
5-) UserInfo Request - Obtaining End User's Information
- The UserInfo endpoint returns information about the logged in user (name, surname, etc.). When the client needs the information of the relevant user, he can obtain the necessary information by using this endpoint. (Note that the relevant user is now authenticated and a request is made to the endpoint using the Bearer Authorization.)
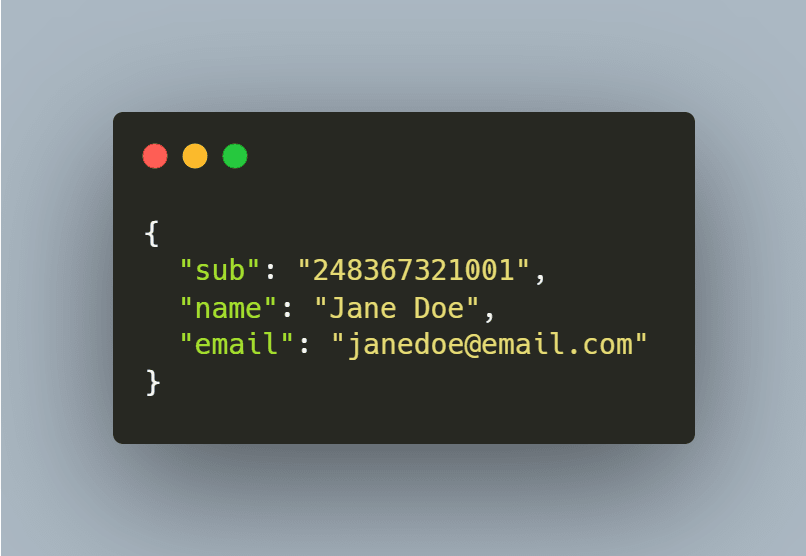
6-) UserInfo Response
If the request that we made in the previous step is successful, the user's information receives.
As another method, the user's relevant information can be accessed by decoding the previously generated "Id_Token" value





Comments
Post a Comment